Purpose-built
data security and privacy software
data security and privacy software
Significantly mitigate risk by automating the finding and securing of sensitive information with our data protection solutions.

Can you redact faster than our tool?
In case of a major system outage, the business continuity team should be contacted using their personal email addresses: Jane Smith (janesmith212121@geoffmail.com) or Fred Jones (fred1782-1@ultramail-b.com) on weeknights and Phil Green (Phil-green@phil-green17.br) or Maria Hernandez (MariaH1776a@brightlightemail.com). For building security use the personal cell phone number to call Brittany Thompson on 555-315-8224 or Jordon Williams on 555-731-3924.
Experience the speed of redaction
Take the challenge

Massive amounts of data, bad actors & increased global regulations
Protecting client, customer & employee data is a necessity. Over the last few years we’ve seen an enormous increase in the amount of sensitive information being collected as well as a proliferation of user data regulations across the globe.
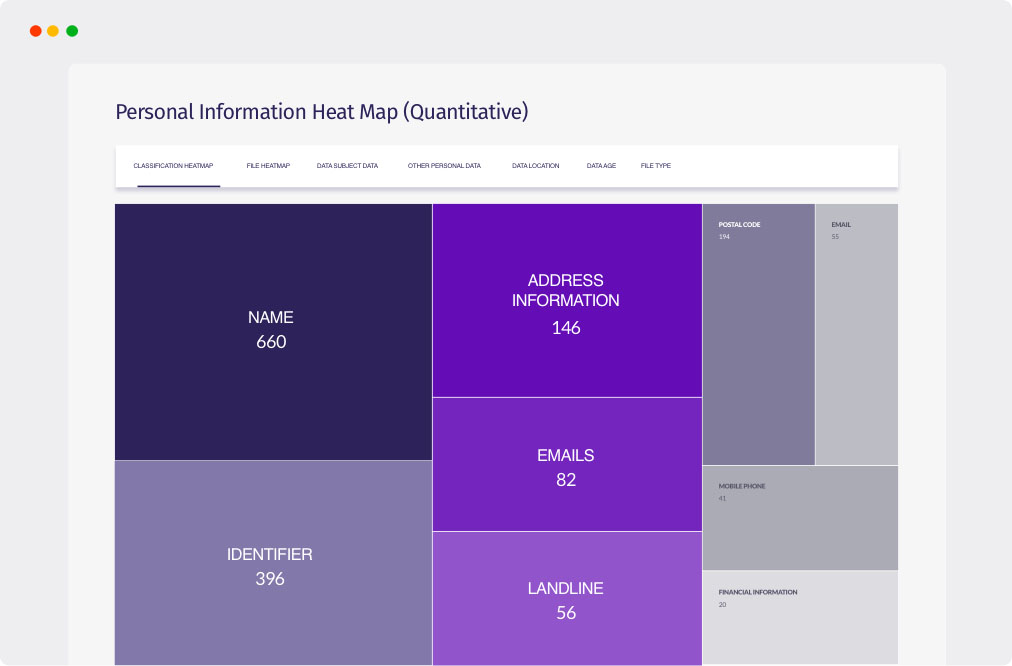
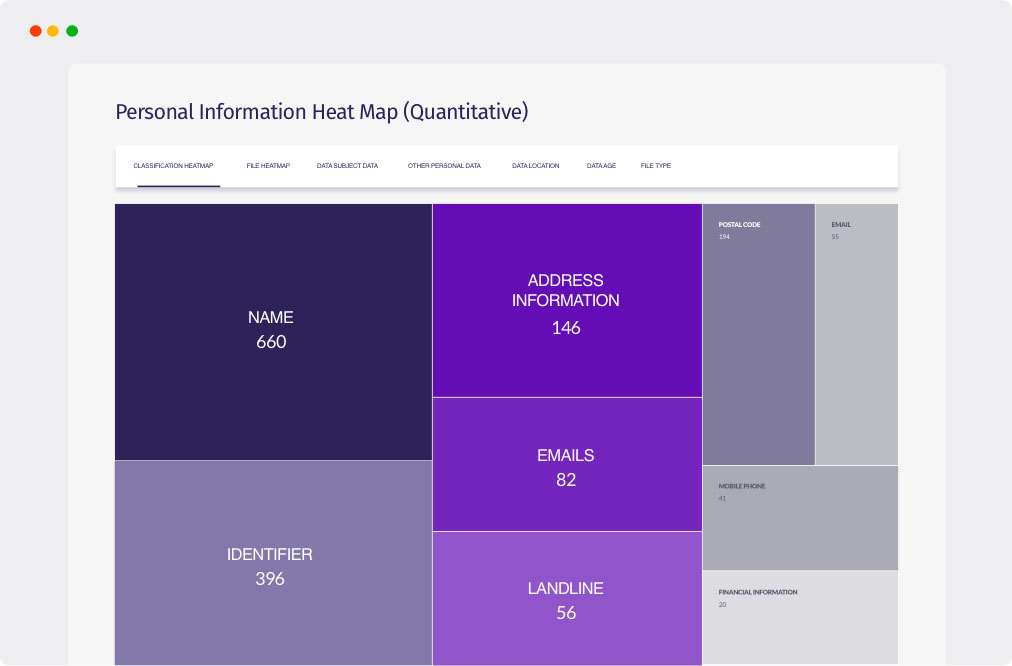
ADDRESS
ANNUAL SALARY
SOCIAL SECURITY NUMBER
18.8
In the first half of 2021, the number of data records exposed during 1,767 data breaches.
$3.8M
Cost of a data breach for a company, and over the next 24 months, more than one-quarter of businesses will experience a recurring material breach.
72 hours
The amount of time your company has to address a data breach before catastrophic damages can occur.
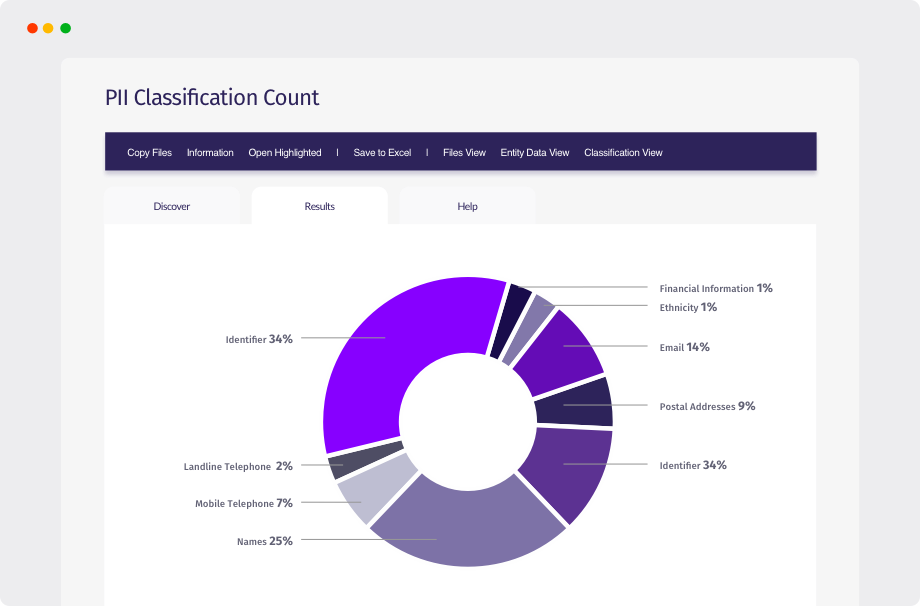
Our proprietary data protection software can be used across a range of departments and job functions within your organization to help locate, secure & control data

93%
quicker than current methods
~$190K
average savings in Year 1
40B+
name combinations recognized
93%
quicker than current methods
~$190K
average savings in Year 1
40B+
name combinations recognized

Address
XXXXXX XXXX, XX
Social security number
XXX-XX-XXXX
Name
xxxxxxx xxxxxxxxxx

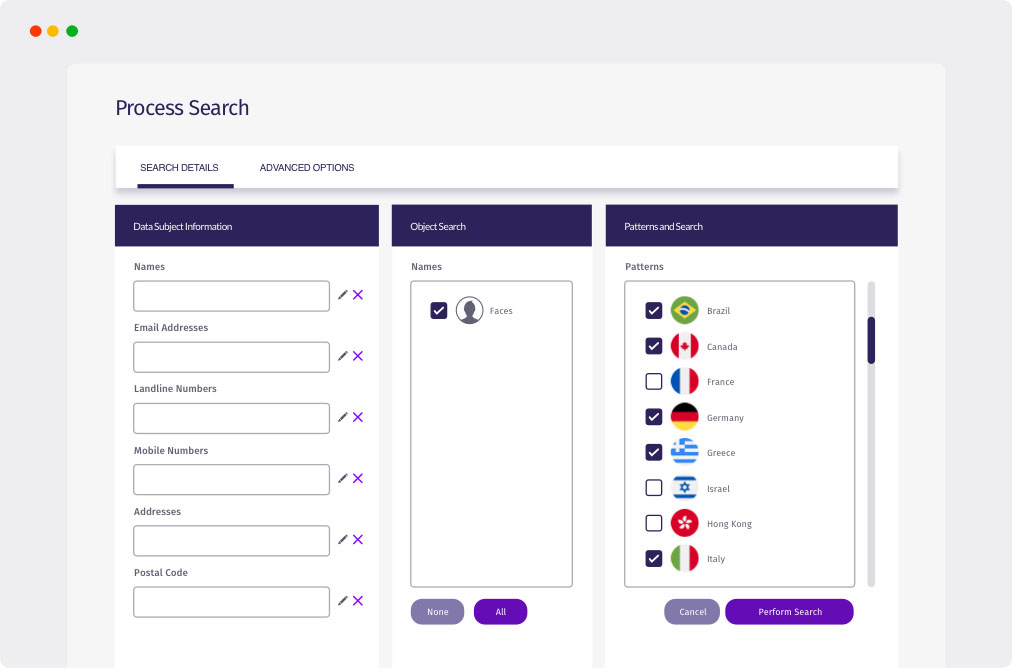
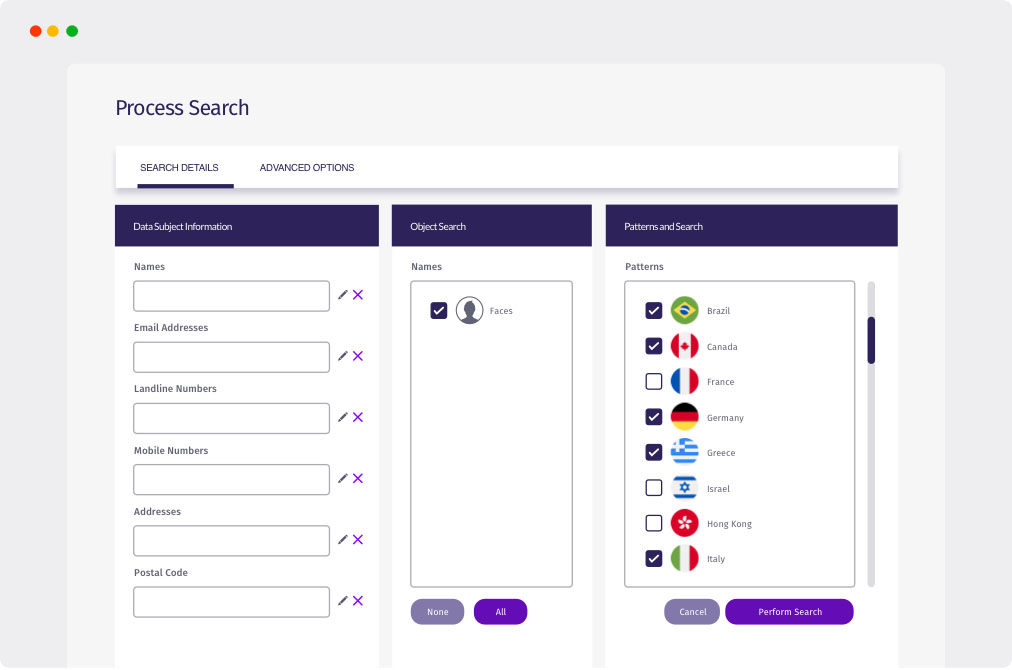
Three steps for protecting your data
Locate
- Automatically scan millions of pages in minutes, avoiding hundreds of hours of human effort
- Leverage pattern matching technology to rapidly locate sensitive information
- Find information held in unstructured file formats located on premise or in the cloud
Secure
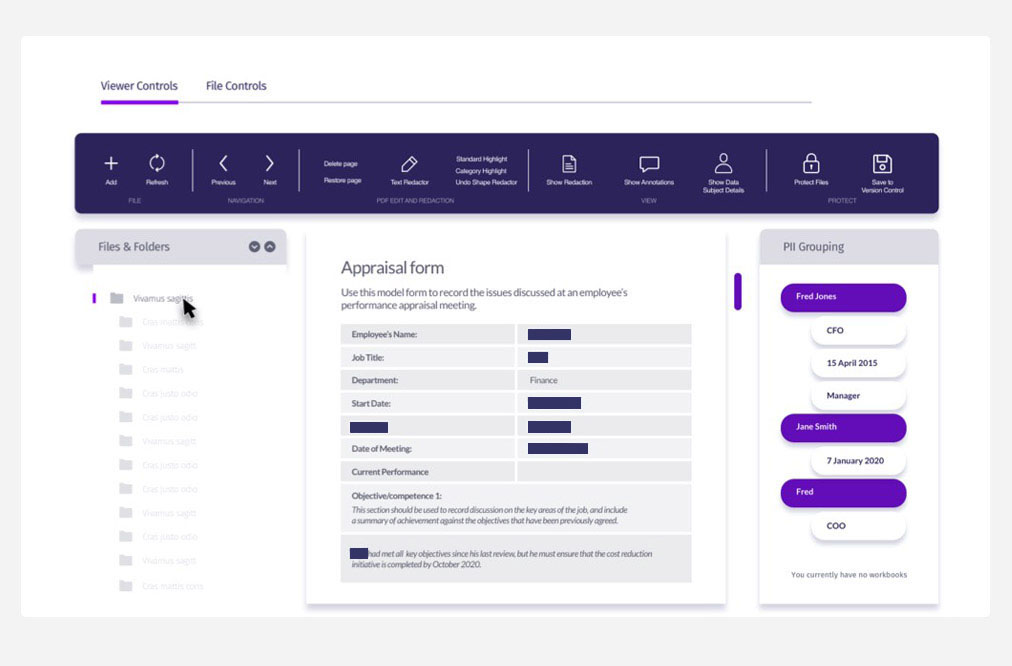
- Apply a redaction mask or anonymization to data files to protect sensitive data including personal information (PI)
- Easily redact third-party information relating to data subjects for governance, risk, and compliance (GRC)
- Leverage tokenized redaction for secure data transfers then remove redactions upon receipt
Control
- Gain ultimate control of the information you hold with our secure data protection solutions
- Extend control beyond digital data to include physical data via approved partners like Mimecast and Relativity
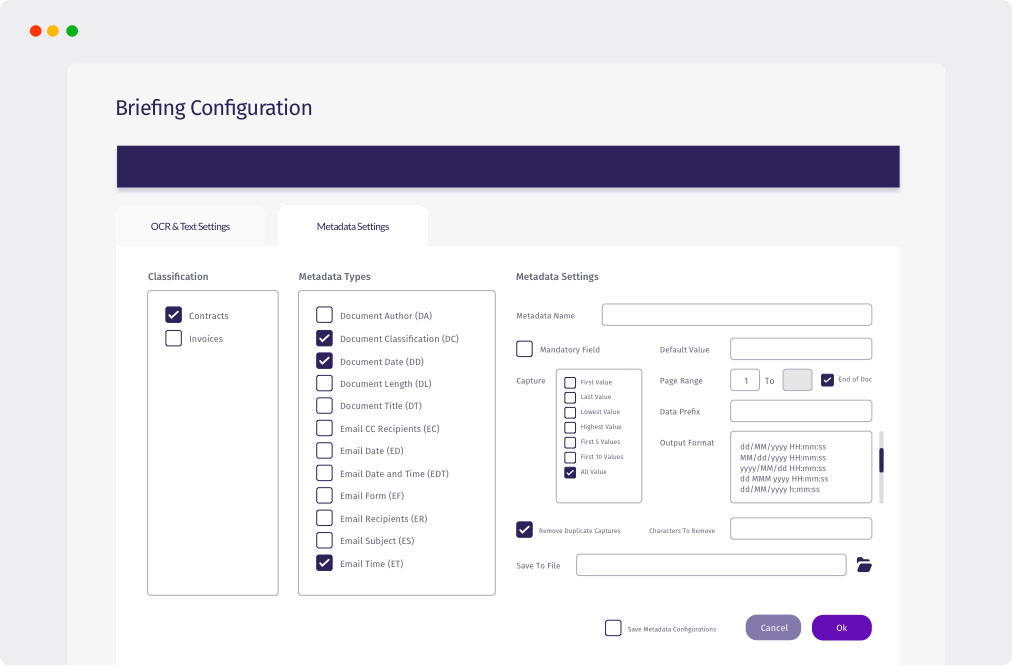
- Classify information to understand what types of PI (e.g., credit card, phone, name, etc.) create risk
Purpose-built solutions for all
your compliance needs
DSAR
Facilitates compliant and timely responses to Data Subject Access Requests (DSARs) by automatically identifying and redacting data subjects and PI.
Indexer
Scans network drives and data repositories in the background to accelerate data subject and PII searches
API
Supports clients seeking to integrate DSAR, PI Protect and Indexer with other software
PI Protect
Finds and anonymizes personal information in unstructured data, including most popular file types, using pattern matching.
Indexer
Scans network drives and data repositories in the background to accelerate data subject and PII searches
API
Supports clients seeking to integrate DSAR, PI Protect and Indexer with other software
Secure the room. Redact the contract.
When you're making a deal, protecting your assets from internal and external threats is vital. With threat levels increasing every day, securing your information requires a combination of advanced prevention and response solutions.
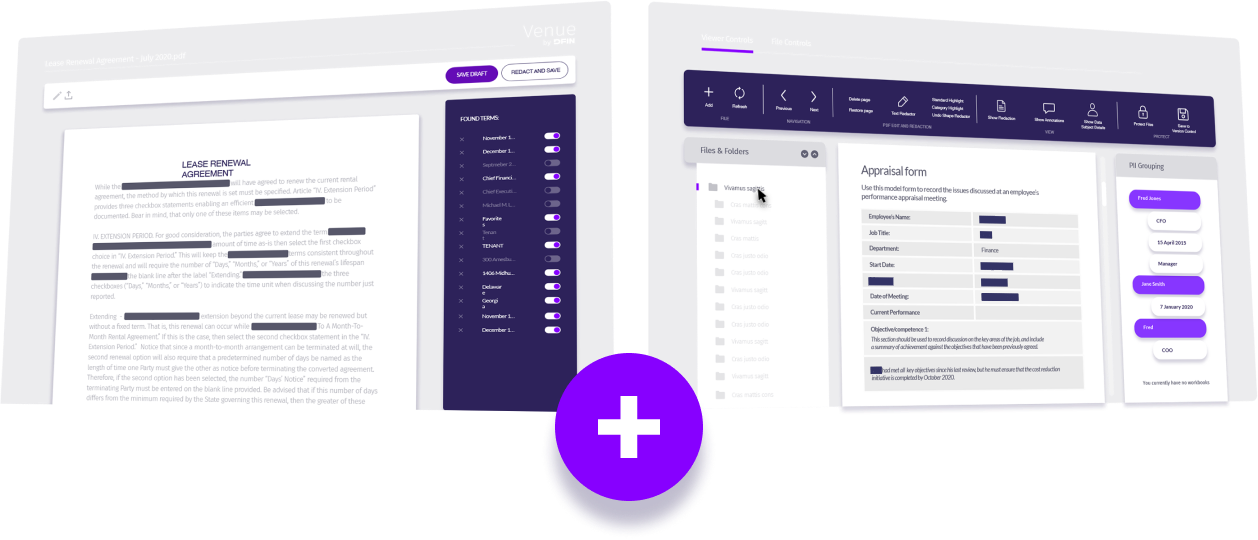

The virtual data
room built for deals

Locate. Secure. Control.
Get the latest on data privacy solutions

DFIN introduces the new Venue, the most modern virtual data room on the market—designed to lead the industry in speed and simplicity

Private Equity's Increased Awareness of Cybersecurity with Darren Wray DFIN's Executive for Data Protect